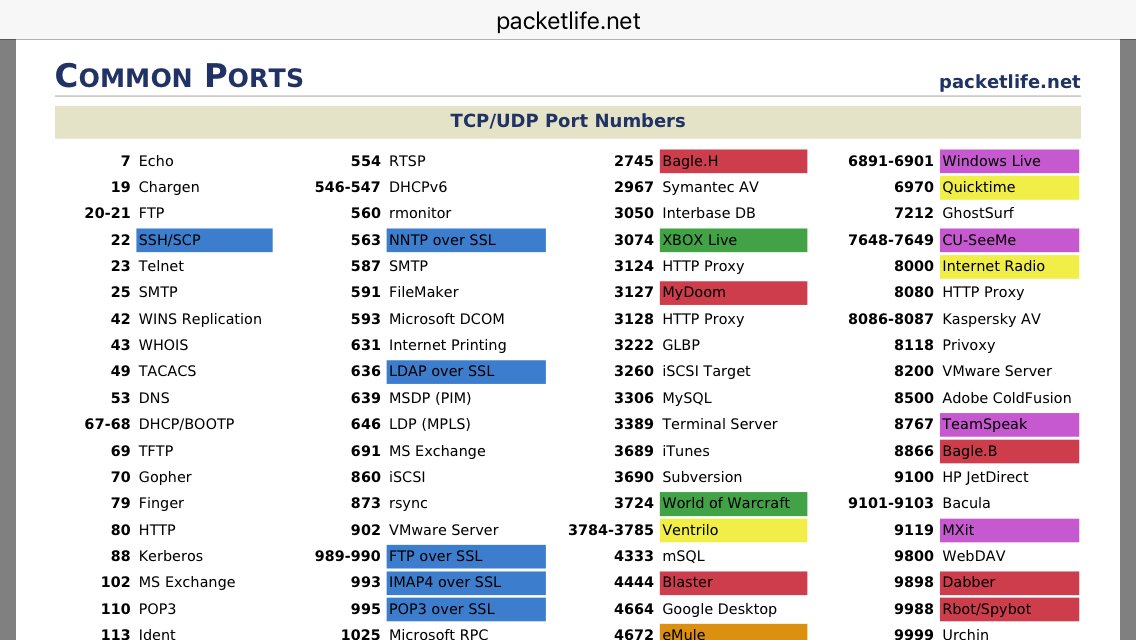
Florian Roth on Twitter: "Common Ports Cheat Sheet via @DanielX4v3r (including Malware ports) https://t.co/i6d5aiFzaf https://t.co/zl9NDVSTEY" / Twitter

How to Disable USB Ports to Prevent Malware Infection | Disable or enable USB ports in computer - YouTube

Ground truth list of TCP ports used for cyberthreats observed on our... | Download Scientific Diagram

ASUSTOR Inc. - Deadbolt Elimination Steps❗ ⚠Ransomware such as Deadbolt and other forms of malware continue to and will always be a risk to your data. Ensure that you have taken the