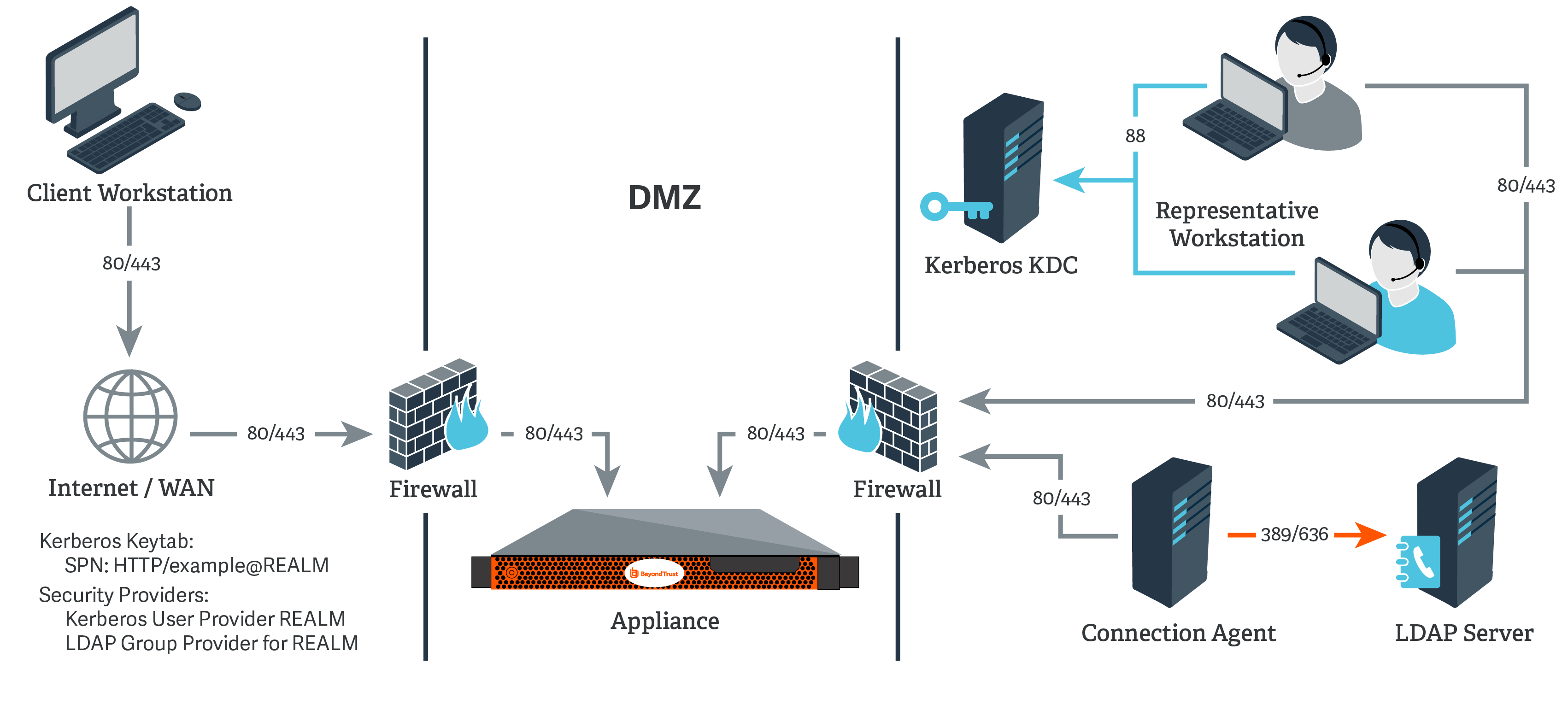
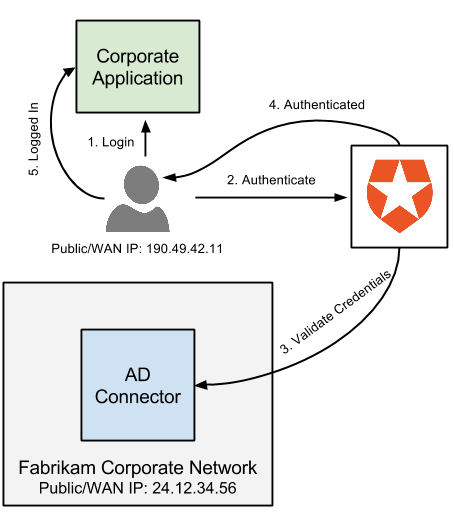
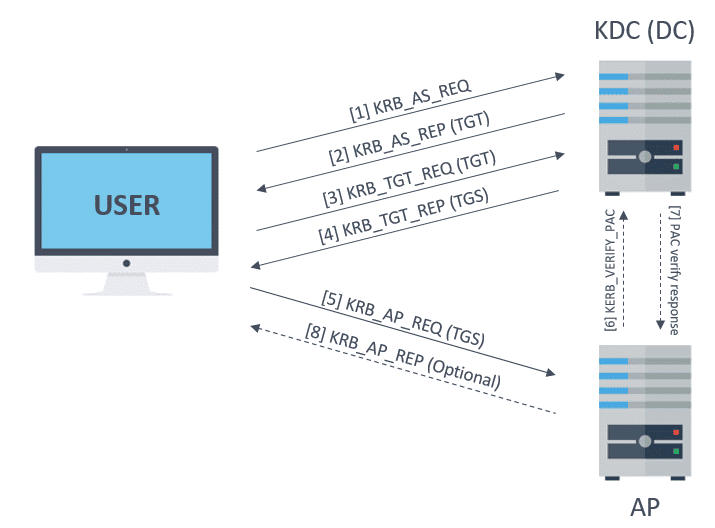
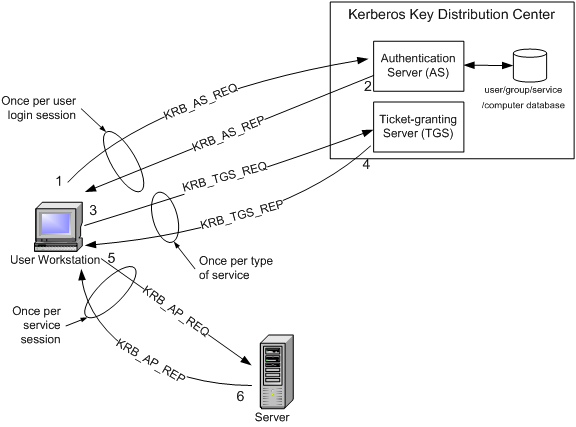
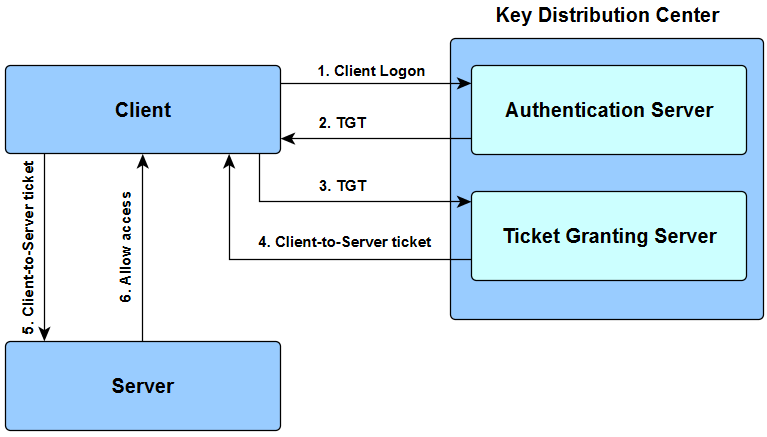
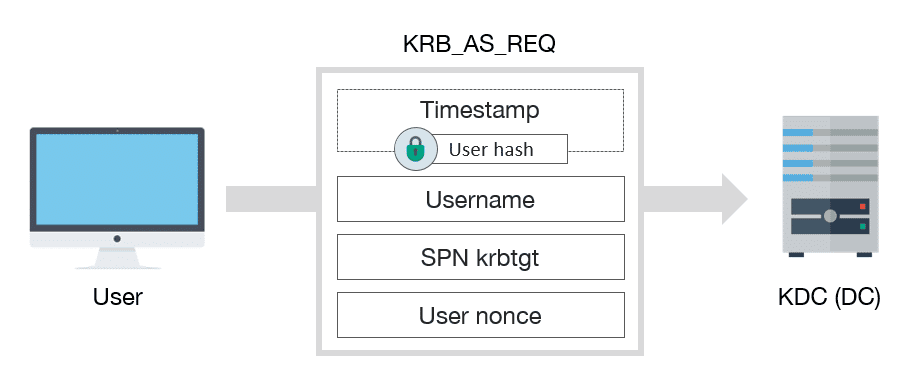
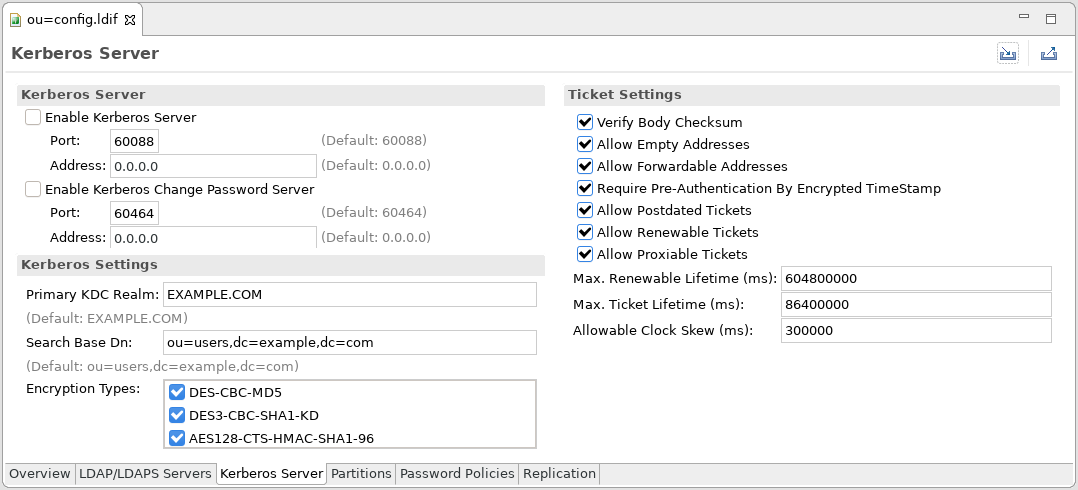
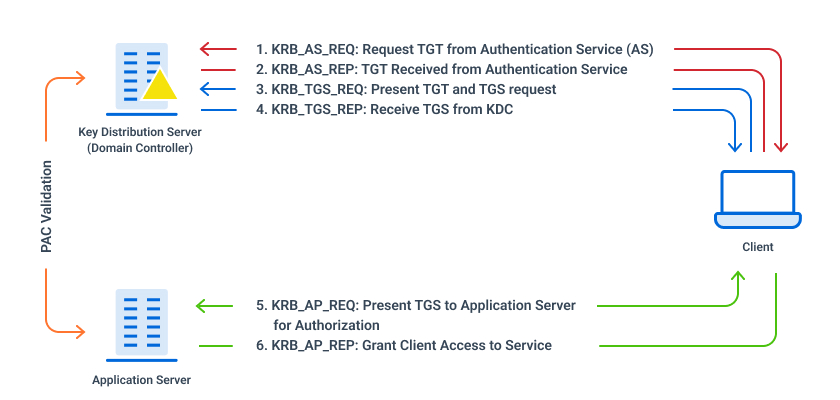
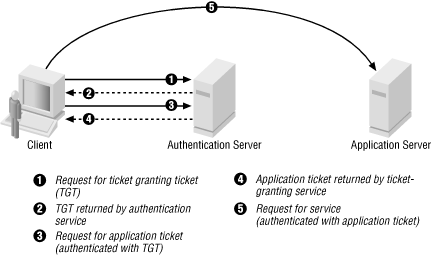
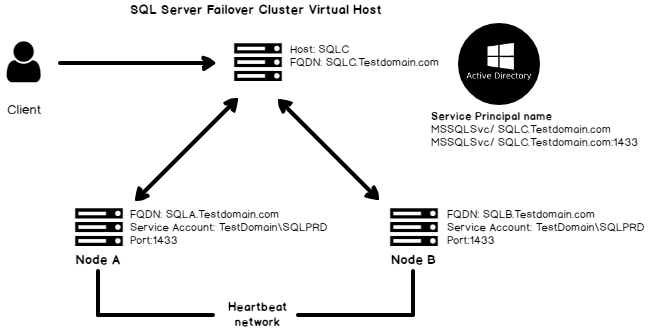
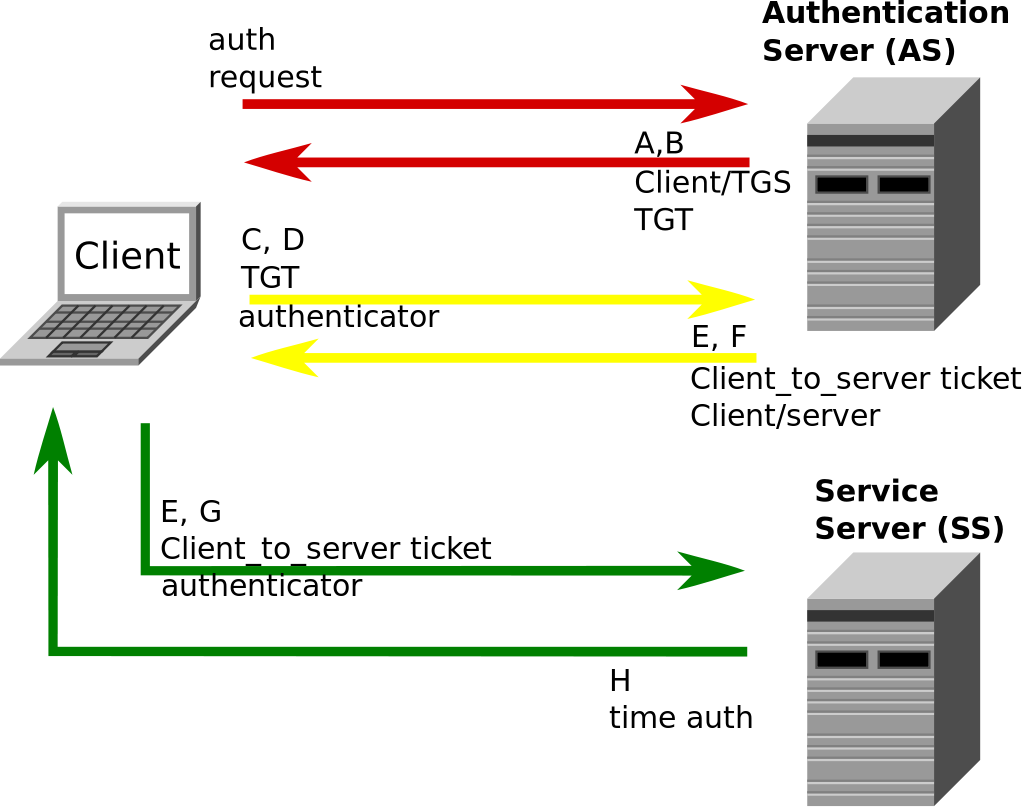
Enabling Kerberos authentication - Asset Reliability | AssetWise APM Wiki - Asset Reliability | AssetWise APM - Bentley Communities

Preparing on-premises and AWS environments for external Kerberos authentication for Amazon RDS | AWS Database Blog